Triggered by fallout from Stuxnet almost a decade ago, Iran has developed a cyber program with robust offensive and defensive capabilities. They have demonstrated competence and a penchant for disruptive attacks in the past. Politics aside, there is a credible reason to maintain a heightened level of diligence, especially as tensions escalate and more activity emanating from Tehran is observed.
The New Attack Surface
Iran has been conducting cyber espionage for years, and they are a strong player in social engineering. It is likely they already have footholds in enterprises large and small and across multiple industries, including some critical infrastructure and the health care system.
Iran has also proven to be adept at weaponizing destructive wiper malware, and this is widely regarded to be the most viable Iranian threat on American targets at the moment. The 2012 attacks on Saudi Aramco, attributed to Iranian actors, saw the Shamoon malware wipe 30,000 devices, and just last month IBM X-force reported that ZeroCleare, a newly discovered wiper, was targeting the industrial and energy sector. The more recent attacks are also believed to be the handiwork of Iranian state-sponsored attackers.
Defense Against the Dark Arts
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued a warning alert on Iranian cyber activity, including a list of mitigation controls (some obvious, some useful). Many of the suggestions, if not previously implemented, involve complex solutions that can't be deployed quickly during an urgent situation. Aim for low hanging fruit and focus efforts on strengthening systems already in place. Increase awareness among users and make sure that they are clear on procedures for reporting anything suspicious.
Offline Backups - The Ultimate Defense
The undeniably most effective mechanism to protect against wiper attacks is the offline backup. Offline means really offline, not in a segregated network or out on the cloud (although those have important advantages too) but truly air-gapped backups. Once a backup system is connected to the network it becomes possible to infiltrate and destroy stored data, resulting in a potentially disastrous loss when both primary and backup copies of data have been deleted. (This appears to be the case with the Sodinokibi ransomware attack on Travelex which has knocked system offline for several days and is currently still in progress).
Data in the cloud and in SaaS apps, should be backed up offline as well, so make sure service providers include this as part of the offering or do it yourself. Remember to keep offline backups in a physically safe location and test restoration periodically as well.
Banks and financial services firms can additionally leverage Sheltered Harbor, which was created to protect customers and financial institutions from catastrophic loss due to cyber attacks or other devastating events.
Neighborhood FBI Agent
Even the largest organizations will need help to protect against a nation-state with virtually limitless resources. Regardless of company size, the time to establish relationships with law enforcement is now, before an attack.
Cut Them Off
Many organizations today operate in a global environment where IP geoblocking is undesirable. Its also important to understand that attacks may originate from anywhere in the world, regardless of who is actually behind them. This makes geoblocking a fairly ineffective tool against an advanced attacker. However, geoblocking can have some benefits as long as it deployed with care not to impede connections that are actually needed. It will almost definitely filter out some bots for network discovery and for automated malware distribution, and in the case of Iran it may be an effective tool against local anti-US hacktivists which are not necessarily state sponsored or particularly sophisticated.
VPNs and remote access systems are an especially good candidate for geoblocking, especially in small to midsize companies where the physical location of most employees can be accounted for. Outbound geoblocking, though less common, may also be effective in disrupting command and control communications.
Final Thought
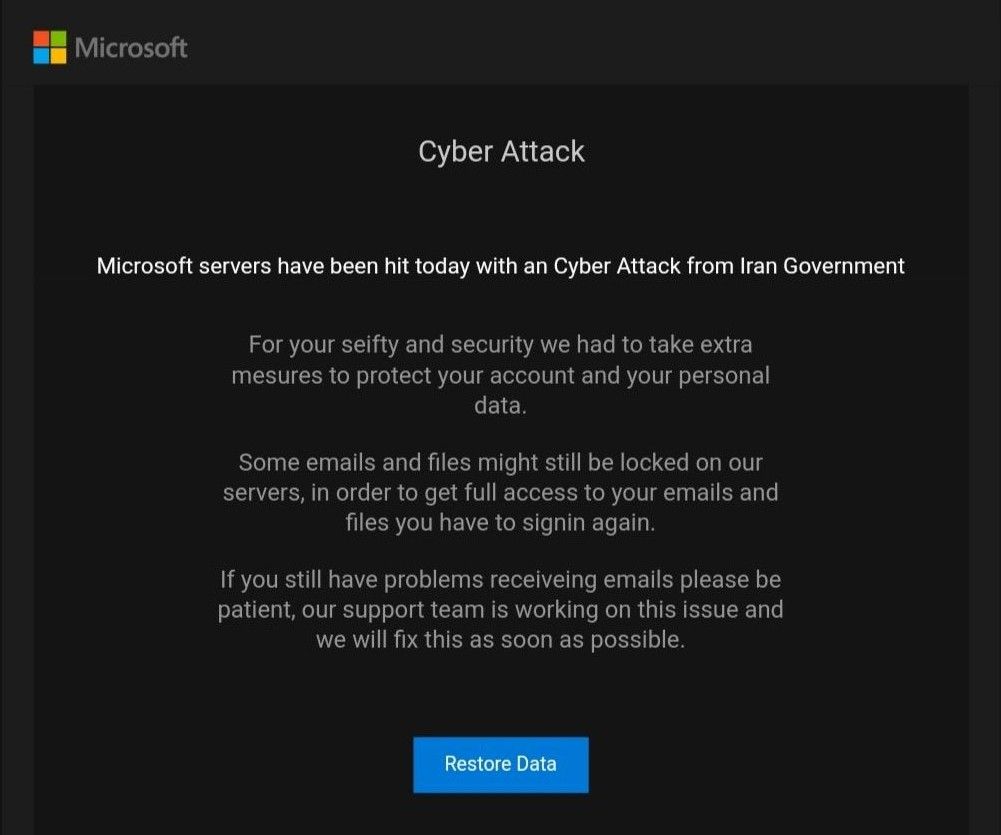
There is no shortage of attackers taking advantage of recent events. As reported on Bleeping Computer, the below phishing scam has been targeting Microsoft email customers. No word yet on whether the perpetrators are from Iran.